The Leader in Supply Chain Automation
30+ years
leading industry innovation
ANNUAL FREIGHT SPEND
MOBILE DOWNLOADS
FLEETS SERVED
Connected technologies to drive actionable insights
IMPROVE CASH FLOW. REDUCE COSTS.
BOOST EFFICIENCY.Our interconnected suite of logistics management software solutions has everything you need for real-time communication and seamless operations.

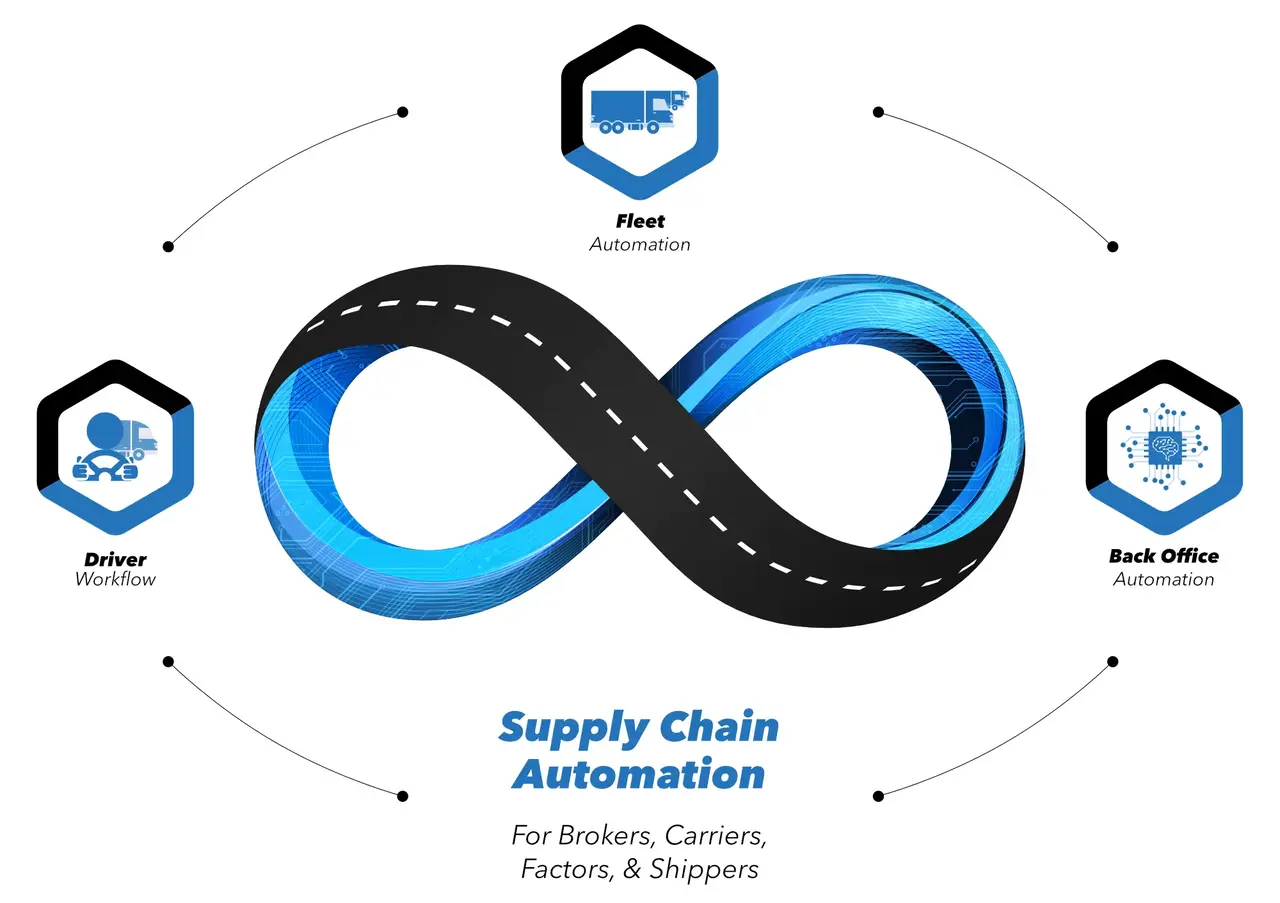
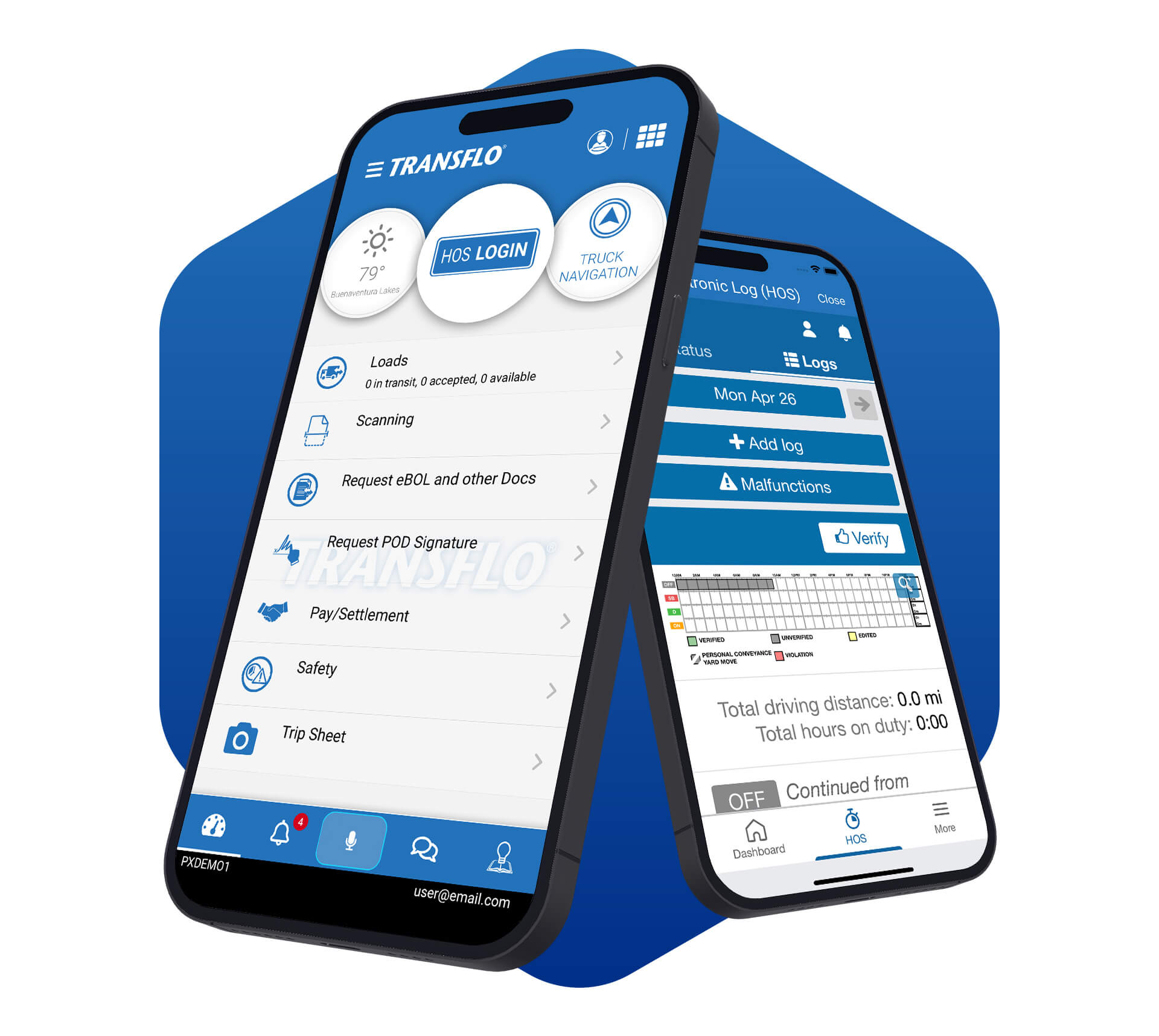
Driver workflow
FOR DRIVERS
One central app for drivers to complete their journey.
Learn about Transflo Mobile+
Fleet automation
FOR THE FLEET
Go beyond HOS with a platform that provides full visibility into your fleet.
Learn about Telematics & ELD
Back-office automation
FOR THE OFFICE
Increase efficiency and reduce up to 97% of paperwork through automation.
Learn about Workflow AI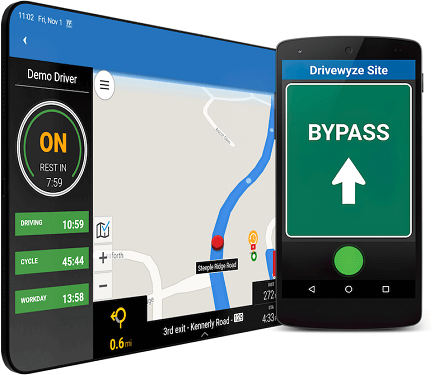
Partners & integrations
ACROSS THE SUPPLY CHAIN
Integrate seamlessly with existing platforms or discover insightful new use cases to drive business forward.
Learn about Partners & integrationsSolutions for every link within the supply chain



A complete ecosystem of logistics management software solutions to manage drivers, loads, routes, documentation, and more.
- Transflo Mobile+
Mobile app for drivers. - Telematics & ELD
Compliance and fleet tracking. - Synergize
Customized document management. - Transflo Express
Truckstop scanning.
Intelligent automated solutions which streamline your invoicing, communications, and load tracking.
- Workflow AI
Back office automation. - Transflo Wallet
Digital payments & fuel advance. - Velocity+
Seamless logistics management.
Operational automation that removes time-consuming manual tasks from your operations.
- Workflow AI
Back office automation.
Connected software that promotes efficiency from fulfillment to delivery.
- Transflo Mobile+
Mobile app for drivers. - Telematics & ELD
Compliance and fleet tracking. - eBOL & ePOD
Paper-free BOL and POD.
Delivering a truckload of benefits
Connect to your TMS
Seamlessly integrate our logistics management software with your existing systems for efficient operations and data flow.
Increase speed to billing
Expedite invoicing processes for faster payment turnaround and improved cash flow.
Reduce costs
Lower operational expenses by automating processes and improving efficiency.
Track everything
Easily monitor payments, loads, and more with intuitive tracking capabilities.
Gain complete visibility
See exactly what’s happening in real time with every shipment and delivery.
Reduce paperwork
Minimize time-intensive manual tasks and paperwork for greater productivity.
Enhance safety
Promote safer driving practices and mitigate risks with safety-focused features.
Simplify compliance
Manage compliance with easy-to-use tools, alerts, and streamlined processes.